In an era where our digital footprints are expanding, securing personal and organizational data against cyber threats is of paramount importance. F-Secure, a leading cybersecurity company, has been at the forefront of safeguarding users and businesses from a wide array of digital threats. In this article, we delve into the features, benefits, applications, and future prospects of F-Secure software solutions to understand why they are essential in contemporary digital security.
Introduction to F-Secure
Founded over three decades ago, F-Secure has established itself as a trusted provider of cybersecurity solutions for both personal and enterprise use. The Finnish company has a rich history of firsts, including the creation of the world’s first heuristic scanner for antivirus programs . Their philosophy is simple: everyone has the right to privacy and security online. This philosophy underpins their diverse product offerings, which range from antivirus and privacy protection solutions to comprehensive cybersecurity services for businesses.
Key Features of F-Secure Software
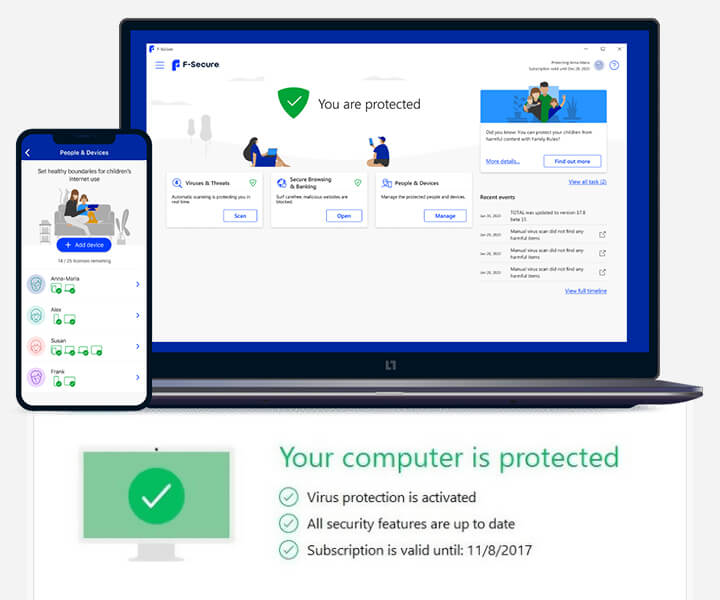
- Comprehensive Antivirus Protection: At the core of F-Secure’s offerings lies robust antivirus protection. The software uses a cloud-based scanning engine to identify and neutralize threats swiftly, ensuring minimal impact on system performance. F-Secure’s DeepGuard technology provides an additional layer by monitoring unknown files for malicious behavior .
- Multi-Device Compatibility: F-Secure products are compatible with multiple operating systems, including Windows, macOS, Android, and iOS. This cross-platform functionality ensures that users can protect all their devices seamlessly .
- Identity and Privacy Protection: To prevent identity theft, F-Secure offers tools like ID monitoring, which scans the dark web for compromised information tied to users’ credentials. Additionally, their VPN service secures internet activity by encrypting data, maintaining privacy and confidentiality online .
- Banking Protection: A standout feature in F-Secure’s suite is its banking protection, which secures financial transactions and blocks access to malicious sites during online banking sessions. This feature is critical for preventing phishing and other forms of online financial fraud .
- Parental Controls: F-Secure includes parental control features that allow parents to manage and monitor their children’s internet usage, setting screen time limits and filtering inappropriate content .
- User-Friendly Interface: Recognizing the need for ease of use, F-Secure’s interface is simple and intuitive, making it accessible for users of all technical skill levels. This approach ensures that advanced security features are easily accessible without overwhelming the user .
Benefits of Using
- Superior Threat Detection and Response: F-Secure is consistently rated highly in independent security tests for its ability to detect and neutralize both known and emerging threats. This ensures that users remain protected against a range of cyber threats, from malware and ransomware to more sophisticated exploits .
- Minimal System Impact: With its cloud-based scanning engine, F-Secure guarantees a minimal impact on device performance, allowing users to run scans and protect their devices without experiencing significant slowdowns or interruptions .
- End-to-End Security Solutions: Beyond antivirus protection, F-Secure provides a holistic suite of products that address various aspects of cybersecurity, including privacy, identity protection, and secure communications, ensuring comprehensive security coverage .
- Reliable Customer Support: Customers have access to a range of support services, including a detailed knowledge base, community forums, and direct assistance from a support team, ensuring that help is available whenever needed .
Applications of F-Secure
- Home Users: For personal users, F-Secure offers protection for individual devices against malware and cyber threats, ensuring safe browsing, banking, and online communication.
- Small to Medium Enterprises (SMEs): SMEs can leverage F-Secure’s business solutions to protect digital assets, maintain regulatory compliance, and ensure secure client data management. The software provides reliable protection without the need for a large in-house IT security team .
- Large Enterprises: For larger organizations, F-Secure provides advanced cybersecurity services, including network protection, endpoint security, and threat intelligence. Their solutions are scalable, adaptable, and integrate smoothly into existing IT infrastructures, making them ideal for complex enterprise environments .
- Mobile Protection: With the increasing use of mobile devices for both personal and business tasks, F-Secure’s mobile protection services ensure that smartphones and tablets are secure from mobile-specific threats such as spyware and malicious apps .
Technical Requirements and Setup
F-Secure solutions are designed to be lightweight and efficient, requiring only the standard system resources available on modern devices. Basic requirements include:
- Windows OS: Windows 8.1 or later
- macOS: Big Sur (11) or later
- Android: Version 8.0 or later
- iOS: Version 15 or later
Installation is straightforward, with intuitive setup processes and automatic updates ensuring that the software is always equipped to tackle the latest threats .
Future Developments and Innovations
As the digital landscape evolves, so too must cybersecurity strategies. F-Secure is investing in machine learning and artificial intelligence to enhance threat detection capabilities and automate responses to cyber incidents. They are also exploring developments in secure cloud environments and enhancing integration with other cloud services to provide comprehensive security solutions for businesses operating in the cloud .
In parallel with technological advancements, F-Secure is actively engaging with global cybersecurity communities and regulatory bodies to shape and influence best practices and policies, ensuring that their users benefit from cutting-edge innovations in digital security .
Conclusion
Navigating the complexities of digital security requires reliable, comprehensive solutions. F-Secure stands out as a robust software suite designed to meet the diverse needs of both individuals and businesses, offering powerful protection against a wide range of cyber threats. With its focus on advanced technology, user-friendly design, and a firm commitment to privacy and security, remains a preferred choice for those seeking robust, reliable cybersecurity solutions. more software